PC Client logs on the domain. Microsoft introduced their version of Kerberos in Windows2000.
Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Microsoft Tech Community
The Kerberos authentication client is implemented as a security support provider SSP and can be accessed through the Security Support Provider Interface SSPI.
Kerberos authentication process windows. To log onto the network the user provides an account name and. What is Kerberos. 3 headed dog 3 heads a client a server and a trusted third party that mediates between the other two.
I did not find much help on googling. In 1980 Greek Mythology. Kerberos Authentication Process In Windows 1.
Can somebody please help. The Kerberos authentication process employs a conventional shared secret cryptography that prevents packets traveling across the network from being read or altered as well as protecting messages from eavesdropping and replay or playback attacks. This is happening because Kerberos requires a Service Principle Name SPN while connecting and before Windows 10 version 1507 and Windows Server 2016 IP addresses couldnt be used as a part of the SPN name the only hostname could be used.
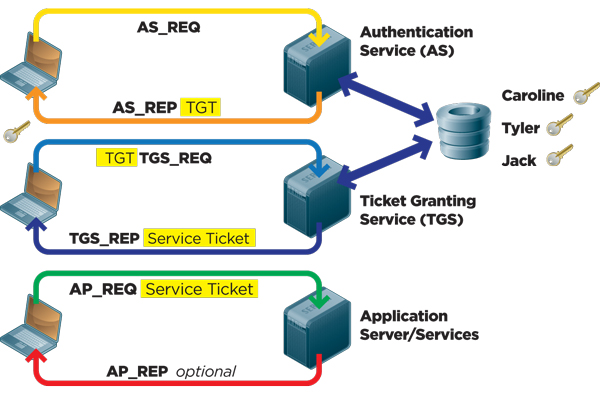
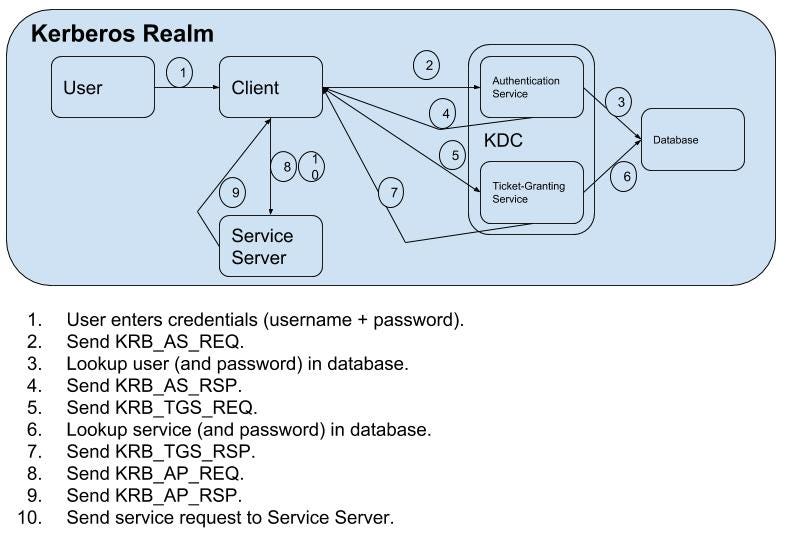
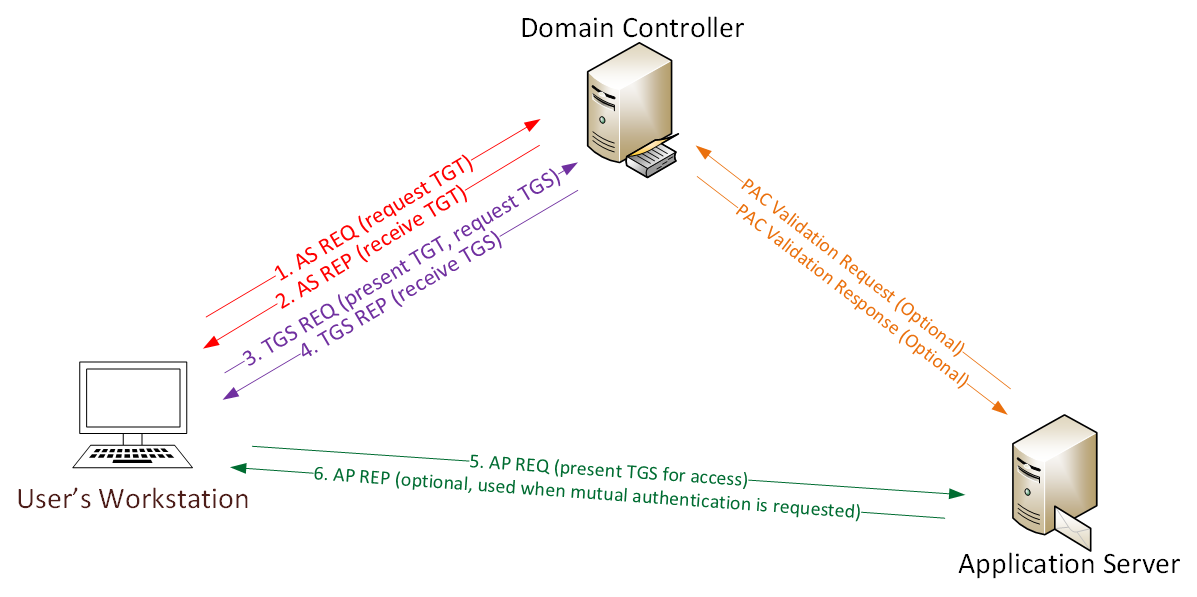
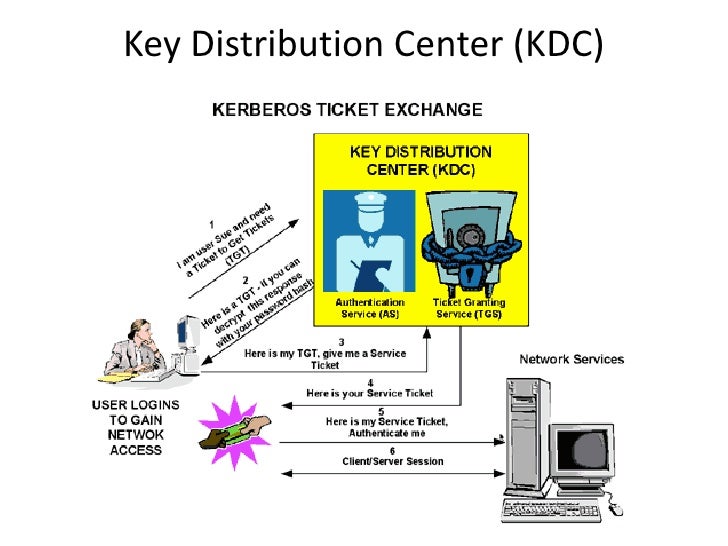
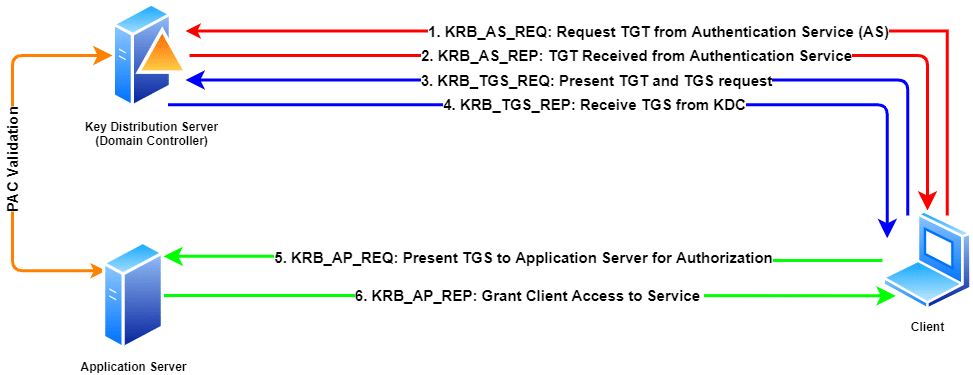
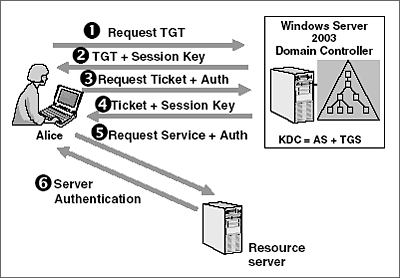
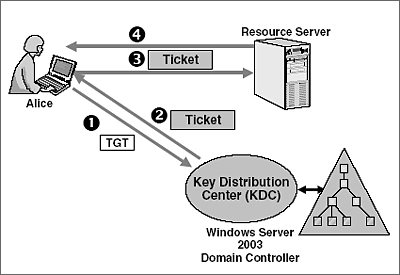
A ticket request for the application server is sent to the Kerberos KDC. Kerberos authentication in windows service. I need to authenticate users from stand alone windows application.
I have the server name username and password ready for it. The Microsoft Windows Server operating systems implement the Kerberos version 5 authentication protocol and extensions for public key authentication. Its preceded generally by java which seems to be called by vpxdexe which is a vCenter process.
That is both the Kerberos-enabled client and server share a secret key. A Ticket-Granting Ticket TGT request is sent to a Kerberos KDC. NTLM authentication was used unlike connecting using the hostname where Kerberos authentication is used by default.
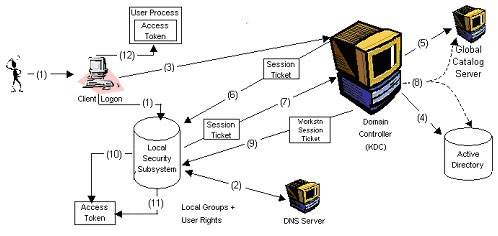
Initial user authentication is integrated with the Winlogon single sign-on architecture. Kerberos Authentication Process In Windows 2. To learn Kerberos authentication through debugging with the KerberosSkeleton project use a PC running Visual Studio VS 2015 as the project is implemented on it.
I am new on kerberos authentication and dont know anything about it. Kerberos works with private key cryptography. Windows Server operating system also implements extensions for public key authentication.
Further digging shows that LSASSexe makes a KERBEROS call to the DC in question once the account is unlocked. The Kerberos KDC returns a TGT and a session key to the PC Client. Kerberos authentication works as follows assuming the client initiates contact with the server.
To authenticate to Kerberos a principal must obtain a ticket by using a password or a keytab file. We can automate this process using the users keytab file by writing a simple script. Kerberos Developed at MIT.
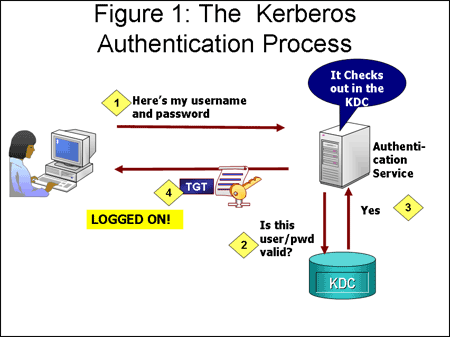
Heres how the log-on process works with Kerberos as the authentication method. The Kerberos authentication client is implemented as a security support provider SSP and can be accessed through the Security Support Provider Interface SSPI. Microsoft implements the KDC as a single process that provides two services.
You can specify a keytab file to use or use the default keytab file of your Kerberos configuration. Kerberos authentication is currently the default authorization technology used by Microsoft Windows and implementations of Kerberos exist in Apple OS FreeBSD UNIX and Linux. A principal is a user or service that can authenticate to Kerberos.
In the Kerberized cluster a Kerberos ticket is required before accessing the cluster services. The Kerberos Key Distribution Center KDC is a domain service running on one or more Domain Controllers. If you want to perform real Kerberos authentication not unit tests make sure you have access to a Windows PC and to a Windows Server PC.
In a Windows 2000 Domain Kerberos authentication is used by both client and a server in trying to determine each others legitimacy. These are the steps in Kerberos Authentication. This topic lists Windows authentication documentation resources for the Kerberos NTLM Transport Layer SecuritySecure Sockets Layer TLSSSL Public Key Cryptography Based User-to-User PKU2U and Digest protocols in addition to links to the security support providers Negotiate and Negotiate Extensions for Windows versions beginning with Windows Server 2003.
Setting up Keberos Auto-Authentication To automate Kerberos authentication we will require the user keytab file.
Kerberos And Windows Security Kerberos On Windows By Robert Broeckelmann Medium
Detecting Forged Kerberos Ticket Golden Ticket Silver Ticket Use In Active Directory Active Directory Security
Kerberos Authentication Process In Windows
What Is Kerberos Understanding Kerberos What Is It How Does It Work
Kerberos Protocol What Every Admin Should Know About Windows Authentication
Kerberos Security In Windows Tutorial
Kerberos Protocol What Every Admin Should Know About Windows Authentication
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com

Kerberos Authentication An Overview Sciencedirect Topics
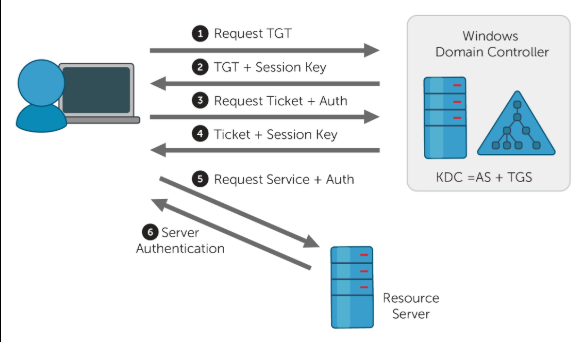
Let S Talk About Kerberos Summary By John D Cyber Jun 2021 Medium
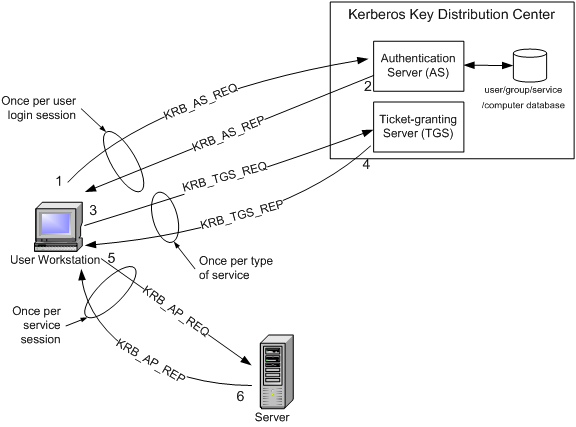
Intel Amt Sdk Implementation And Reference Guide
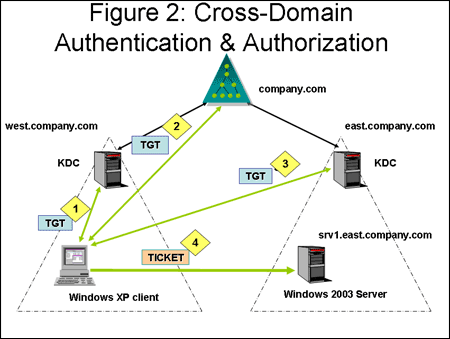
Kerberos Protocol What Every Admin Should Know About Windows Authentication
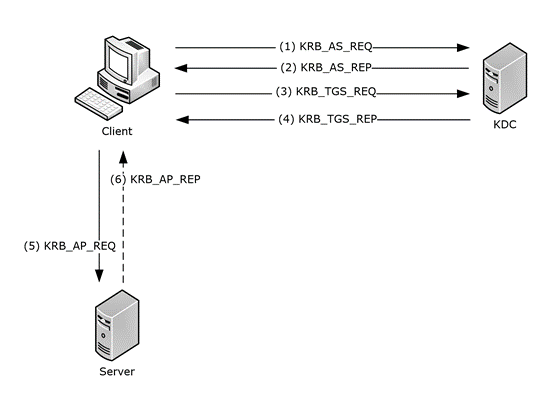
Ms Kile Kerberos Network Authentication Service V5 Synopsis Microsoft Docs
Five Steps To Using The Kerberos Protocol
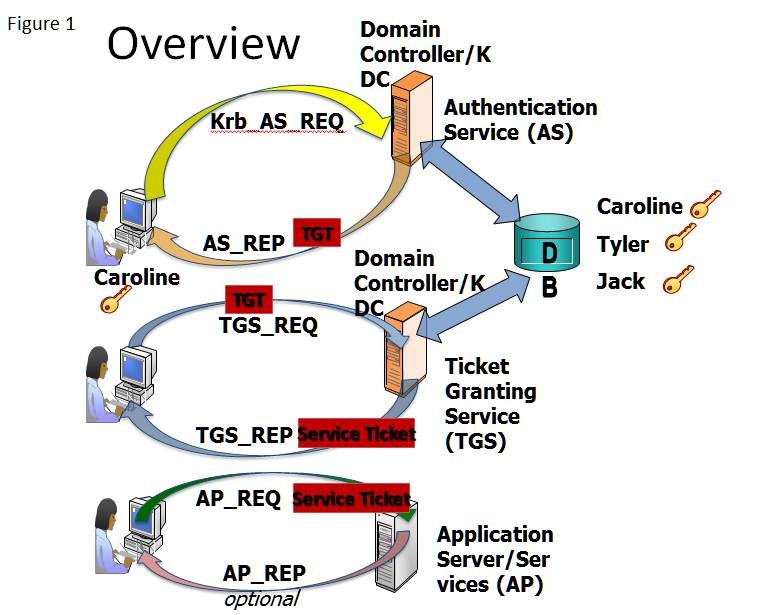
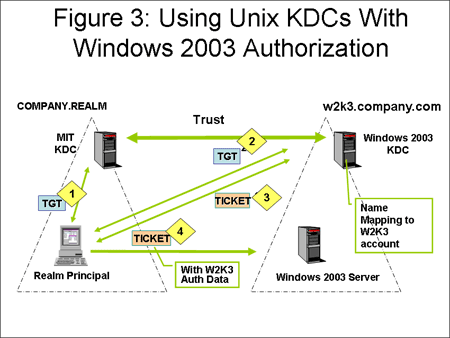
Kerberos Platform Interoperability Connects Windows To The Rest Of The World
Logging On To Windows Using Kerberos Single Domain Environment

The Kerberos Ticket Instant Refresh And Security Legacy Protocols Seven It Blog

Kerberos Authentication Flow For Browser Based Applications Provided By The As Abap Sap Blogs


