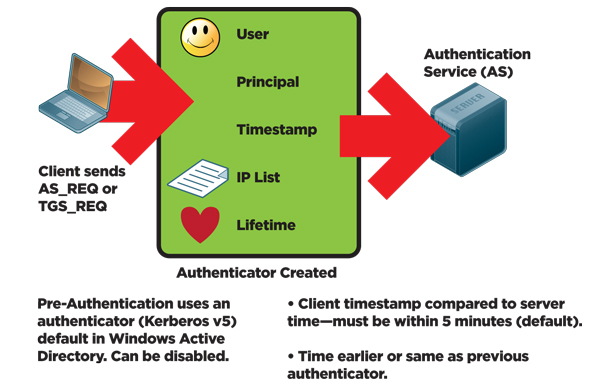
KPT enables clients that are unable to get Kerberos tickets from the domain controller to pass through a service that transitions the clients authentication into a true Kerberos authentication request. Kerberos authentication supports a delegation mechanism that enables a service to act on behalf of its client when connecting to other services.

Kerberos Authentication Sikigroups
This paper gives an overview of the Kerberos authentication model as implemented for MITs Project Athena.

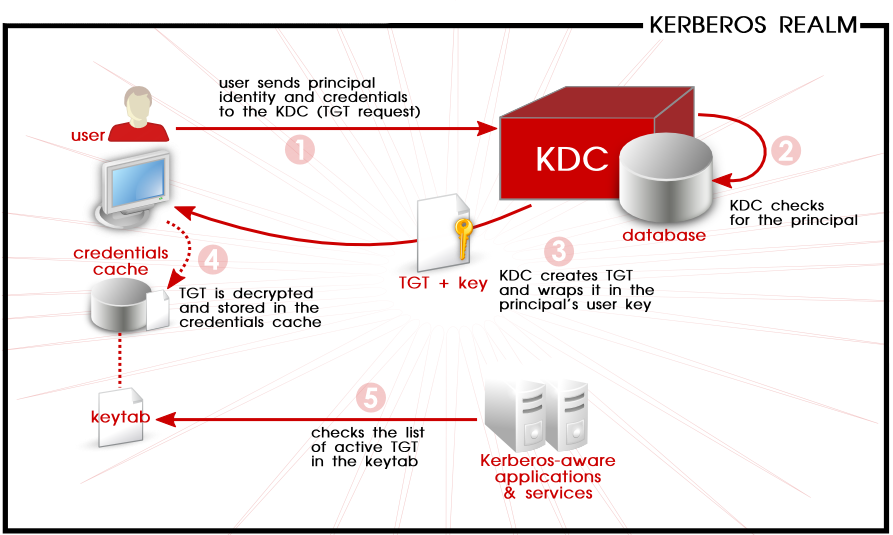
Kerberos authentication service uses the concept of. Using Kerberos authentication within a domain or in a forest allows the user or service access to resources permitted by administrators without multiple requests for credentials. Kerberos runs as a third-party trusted server known as the Key Distribution Center KDC. The KDC contains a secret shared with the principal.
In this article we will see discussed the Kerberos concept. Negotiate is a. Kerberos provides an alternative approach whereby a trusted third-party authentication service is used to verify users identities.
When authenticating Kerberos uses symmetric encryption and a trusted third party which is called a Key Distribution Center KDC. In order to setup Kerberos for the site make sure Negotiate is at the top of the list in providers section that you can see when you select windows authentication. Kerberos is a computer network authentication protocol.
It delegates those to the services. After initial domain sign on through Winlogon Kerberos. Kerberos is a distributed authentication service that allows a process a client running on behalf of a principal a user to prove its identity to a verifier an application server or just server without sending data across the network that might allow an attacker or the.
In the scenario presented above the KPT role is played by the load balancer or application delivery controller. It is designed at MIT to allow network resources in a secure manner. It has also become a standard for websites and Single-Sign-On implementations across platforms.
It uses secret-key cryptography and a trusted third party for authenticating client. It might also use NTLM which is also a provider in windows authentication. The protocol to authenticate callers is one of those low level details found in text books.
What is important to know is that. At the moment of the authentication Kerberos stores a specific ticket for that session on the users machine and any Kerberos aware service will look for this ticket instead of prompting the user to authenticate through a password. It is designed at MIT to allow network resources in a secure manner.
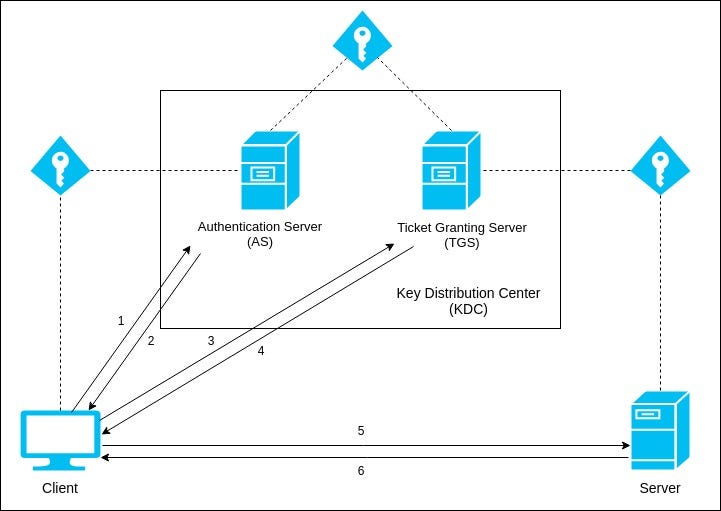
Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network like the internet. In Kerberos Authentication server and database is used for client authentication. This is network-accessible service which runs in the KDC and which is used to authenticate callers.
The Kerberos protocol is designed to provide reliable authentication over open and insecure networks where communications between the hosts belonging to it may be intercepted. It describes the protocols used by clients servers and Kerberos to achieve authentication. Kerberos authentication is currently the default authorization technology used by Microsoft Windows and implementations of Kerberos exist in Apple OS FreeBSD UNIX and Linux.
Last Updated. Microsoft introduced their version of Kerberos in Windows2000. 3 Enabling windows authentication doesnt mean Kerberos protocol will be used.
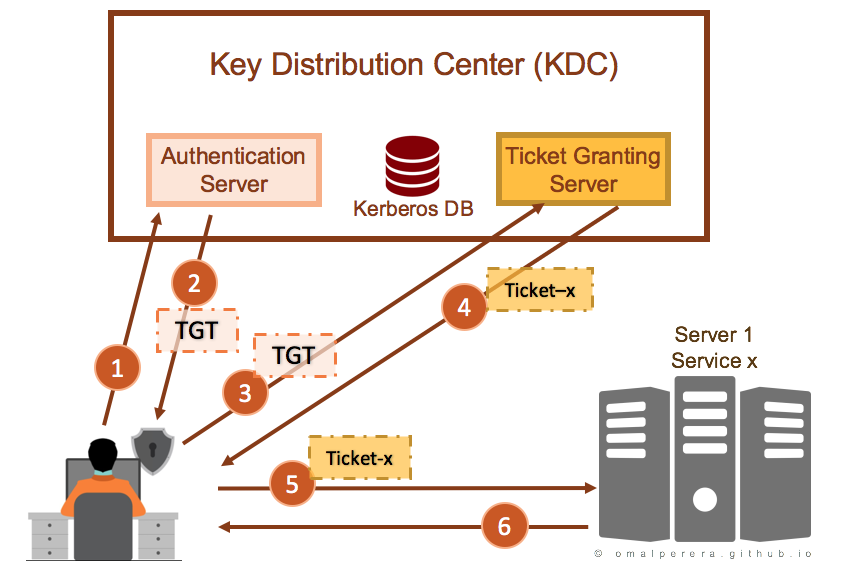
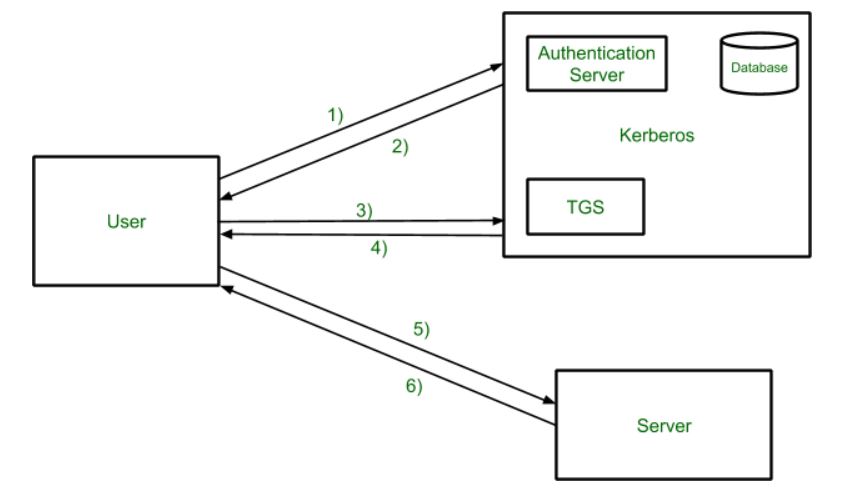
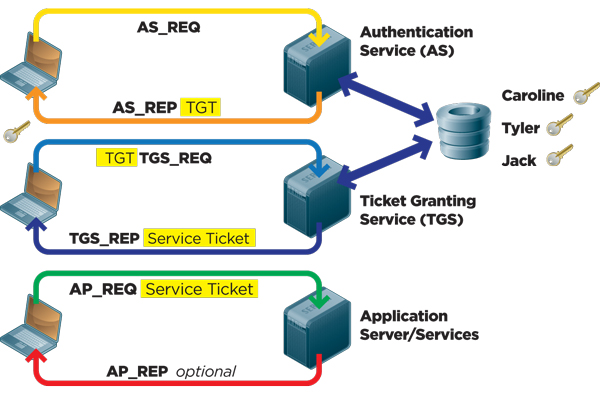
17 Sep 2020 Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. Center KDC also known as the Kerberos server is composed of the authentication server and the ticket-granting server. It is important that you use a secure machine.
As Kerberos is only dealing with Authentication it does neither Authorization the step of granting or denying access to a service based on the user wishing to use it nor Accounting account and session management as well as logging. The authentication server issues ticket-granting tickets and the ticket-granting server issues service tickets.
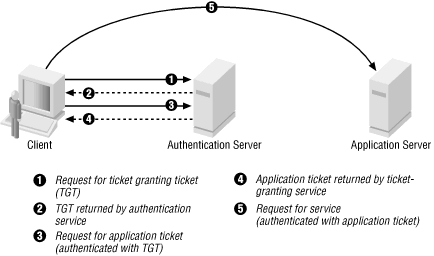
Understanding Kerberos Concepts Ldap Sso Authentication 3 1 Documentation
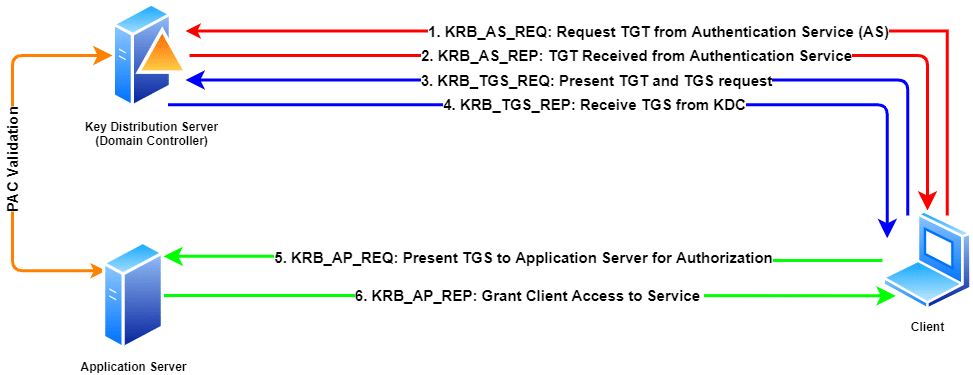
What Is Kerberos Understanding Kerberos What Is It How Does It Work
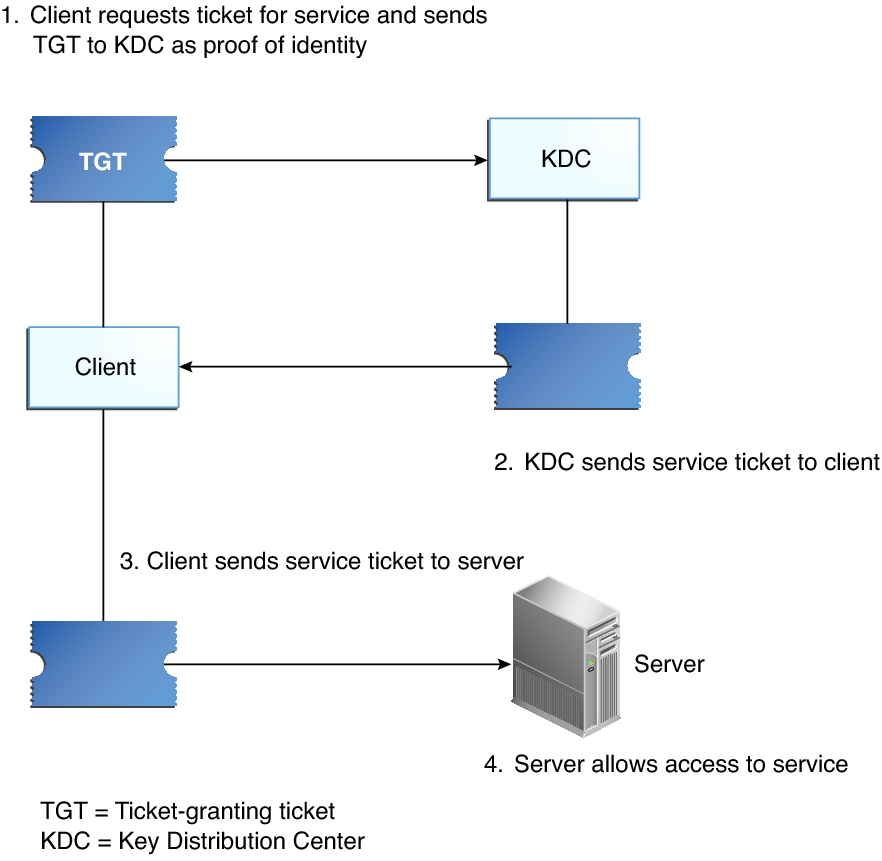
How The Kerberos Service Works Managing Kerberos And Other Authentication Services In Oracle Solaris 11 3
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com

Kerberos Authentication An Overview Sciencedirect Topics
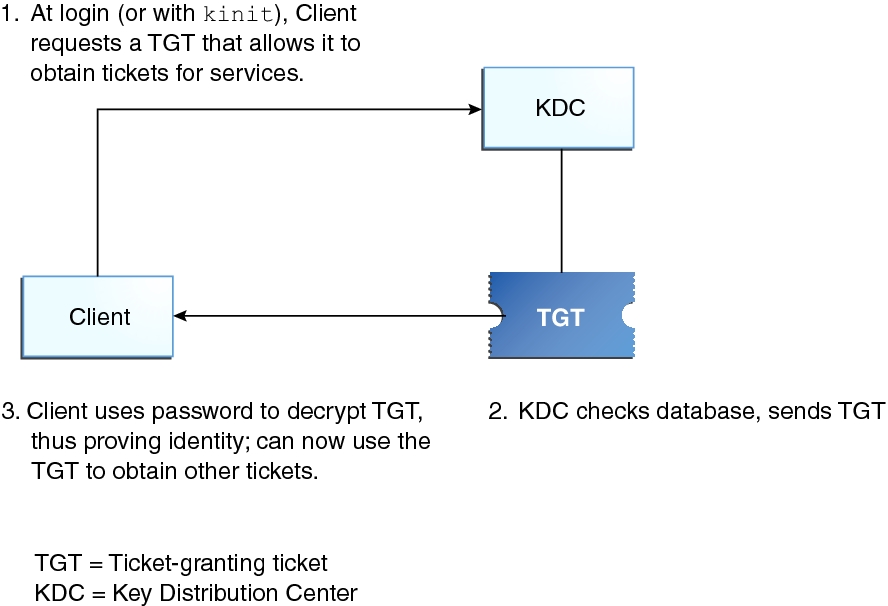
How The Kerberos Service Works Managing Kerberos And Other Authentication Services In Oracle Solaris 11 3

Api Gateway As A Kerberos Service Axway Open Documentation
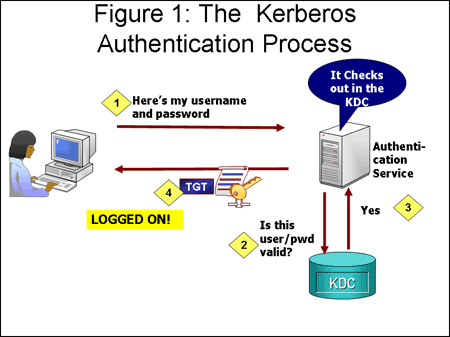
Kerberos Authentication Protocol Blog On Information Security And Other Technical Topics
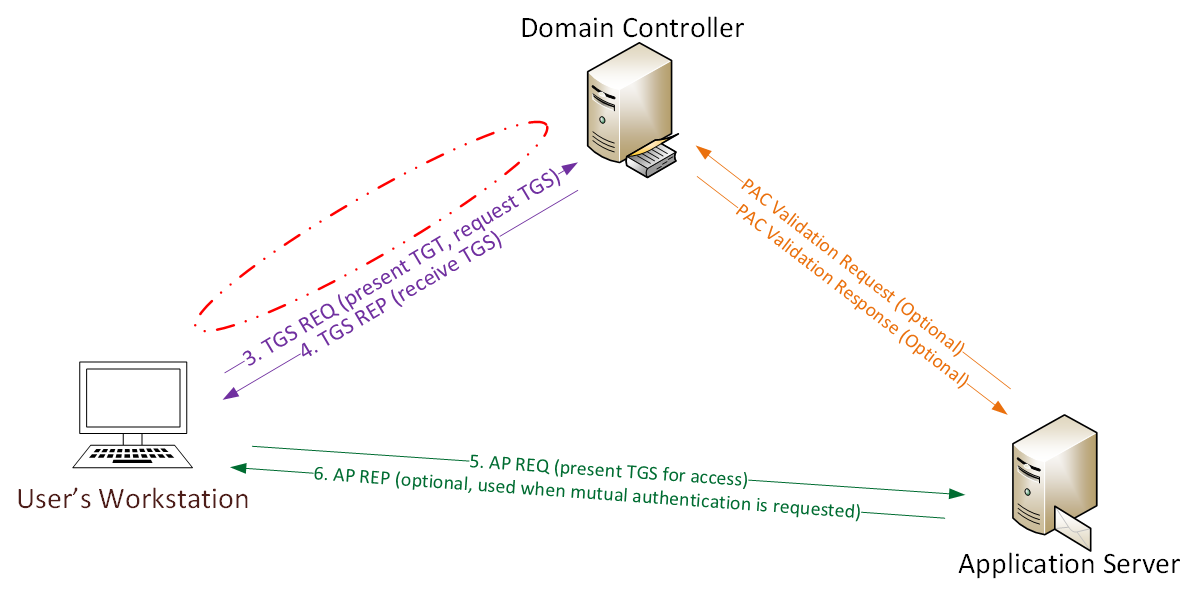
Detecting Forged Kerberos Ticket Golden Ticket Silver Ticket Use In Active Directory Active Directory Security
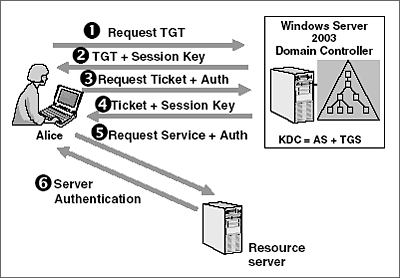
Five Steps To Using The Kerberos Protocol

Kerberos Protocol Wikipedia Republished Wiki 2
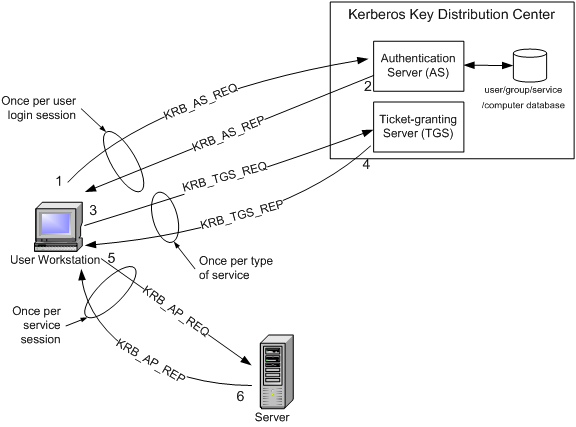
Intel Amt Sdk Implementation And Reference Guide
Kerberos Authentication Protocol Kerberos Is A Strong Network By Nipuna Dilhara Medium
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
Chapter 3 Using Kerberos Red Hat Enterprise Linux 6 Red Hat Customer Portal